Highly specialized question, but trying anyway...
Hello guys, I'm new here, have recently come over from CrackBerry forums (on the same login, that's pretty neat, excuse the profile picture though :rotfl , so please don't be too hard on me.
, so please don't be too hard on me.
For Christmas, I've got a brand new iPhone 4S 64GB with iOS 6.1.3 installed to replace the same iPhone I lost clubbing in October.
Since then, our home Wi-Fi has been upgraded to use super-secure WPA2-Enterprise encryption with RADIUS authentication, because our Wi-Fi previously was open with no encryption, and had a hotspot log-in page to authenticate users. But this was easily bypassable, so it needed to be upgraded. WPA2-Personal encryption was trialled, but abandoned after testing it and having a 100% success rate in cracking the WPA2 key (tested on my own setup - don't worry, it's ethical) using BackTrack Linux. So, WPA2-Enterprise was chosen and the equipment was upgraded, and configured.
Back over at CrackBerry, I was able to install the required certificates and connect on BlackBerry devices without an issue. However, when it comes to iOS, it's not pretty.
Despite installing my self-signed root certification authority, I am having issues getting devices running iOS 4, iOS 6 and iOS 9 to trust the certificate provided by the RADIUS server. Windows laptops and BlackBerry tablets/smartphones don't have an issue here, and verify the certificate as intended, completing the Wi-Fi connection.
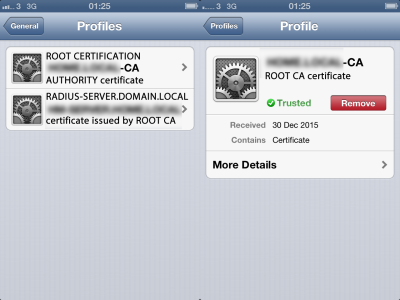
Here's some (censored) screenshots of the 'Profiles' installed...
But when I try to connect to the network, after entering the username and password, I get this...
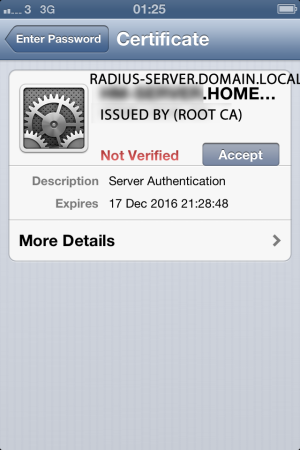
It should trust this certificate, because the root CA is installed as a profile right?
You can still connect, but this leaves iPhone vulnerable to an attack where someone sets up a rogue WPA2-Enterprise access point, but with a different certificate. The point of the certificate being trusted would prevent this from happening, because the certificate presented by the rogue access point would not be trusted... if only iOS would trust my genuine certificate!
Has anybody else got similar experiences with this?
Does anybody at their university use 'Eduroam'? This Wi-Fi network uses the same authentication system as ours, so did you have this issue too? To find out, 'forget' then network, then join it again then after entering your credentials, see if you get a similar 'not verified' warning message.
Please let me know.
Thanks.
Hello guys, I'm new here, have recently come over from CrackBerry forums (on the same login, that's pretty neat, excuse the profile picture though :rotfl
For Christmas, I've got a brand new iPhone 4S 64GB with iOS 6.1.3 installed to replace the same iPhone I lost clubbing in October.
Since then, our home Wi-Fi has been upgraded to use super-secure WPA2-Enterprise encryption with RADIUS authentication, because our Wi-Fi previously was open with no encryption, and had a hotspot log-in page to authenticate users. But this was easily bypassable, so it needed to be upgraded. WPA2-Personal encryption was trialled, but abandoned after testing it and having a 100% success rate in cracking the WPA2 key (tested on my own setup - don't worry, it's ethical) using BackTrack Linux. So, WPA2-Enterprise was chosen and the equipment was upgraded, and configured.
Back over at CrackBerry, I was able to install the required certificates and connect on BlackBerry devices without an issue. However, when it comes to iOS, it's not pretty.
Despite installing my self-signed root certification authority, I am having issues getting devices running iOS 4, iOS 6 and iOS 9 to trust the certificate provided by the RADIUS server. Windows laptops and BlackBerry tablets/smartphones don't have an issue here, and verify the certificate as intended, completing the Wi-Fi connection.
Here's some (censored) screenshots of the 'Profiles' installed...

But when I try to connect to the network, after entering the username and password, I get this...

It should trust this certificate, because the root CA is installed as a profile right?
You can still connect, but this leaves iPhone vulnerable to an attack where someone sets up a rogue WPA2-Enterprise access point, but with a different certificate. The point of the certificate being trusted would prevent this from happening, because the certificate presented by the rogue access point would not be trusted... if only iOS would trust my genuine certificate!
Has anybody else got similar experiences with this?
Does anybody at their university use 'Eduroam'? This Wi-Fi network uses the same authentication system as ours, so did you have this issue too? To find out, 'forget' then network, then join it again then after entering your credentials, see if you get a similar 'not verified' warning message.
Please let me know.
Thanks.
Last edited:


